Author: Manu Steens
In this post I write my own opinion, not that of any organization.
What is the issue?
For example, when you start with operational and tactical risk management, training is always useful. In addition to being in the books with your nose, it is good to go into the mud with the bones and gain first experiences. For those first experiences to have an elementary contribution, they must reach the minimum baseline. So, the basic tasks. But what are they? How do you go about it?
Contents
How do you go about it? The basic tasks.
You get both the basic tasks and a whole operational risk management system from the description of ISO31000 or other standards.
The basic tasks include:
- Determining the goals
- Determination of the processes and projects for those purposes
- Determining the risks of those processes and projects, in terms of threats and opportunities
- Evaluating and prioritizing those risks
- Determine, implement, and follow up on measures.
- Report.
What is there to do? Helicopter explanation.
I now explain these basic tasks:
Determining the goals
The goals or objectives of the organization arise from the mission and vision statements of the organization and are unique to that organization. These objectives are set by the founders of the organization and can be updated depending on the interpretation of the mission and vision in the changing environment in which the organization performs. Normally, one can find these goals in the organization’s strategic and operational objectives documentation.
Determination of the processes and projects for those purposes
Top management translates these strategic and operational objectives into processes, projects and services and products. These you can also find in the policy documents of the organization, often also indirectly on their website.
Determining the risks of those processes and projects, in terms of threats and opportunities
This is where the ‘real’ and original contribution of the risk manager in collaboration with the project leaders, process owners and service providers begins.
Regardless of whether it concerns a process, project, or service, many risk analyses can be carried out with a bow-tie analysis.
To this end, a risk is written out as a risk statement that consists of three parts: a cause, an event, and the effect thereof. Based on this statement, the following things will happen in order:
- Determine the probability of the causes.
- Determine the corresponding probability of the event.
- Determine all the impacts of the consequences of the event.
Evaluating and prioritizing those risks
To be able to estimate these things, there are of course definitions in advance of how you look at opportunities, what types of impacts you look at, and their magnitudes. In addition, you also define a risk matrix, which is based on two axes: one for the total probability and one for the maximum impact of the event.
Possible definitions for probability can be a percentage, or a frequency of occurrence. Possible types of impacts are financial damage, health damage, legal damage, reputational damage, etc.
A commonly used type of matrix is a 5×5 matrix, in which opportunities and impacts are plotted. This matrix is usually limited to a threat matrix. However, the same principle is possible for opportunities. Then it could be a 5×10 matrix. One uses color codes where green means that it is good, and red means action required. In the case of red, one can then propose a maximum time within which a solution must be implemented. For threats to mitigate them. At opportunities to ensure that they perform to the maximum.
Such a 5×10 matrix then looks like this: (on the left the opportunities, on the right the threats, vertically the probability)
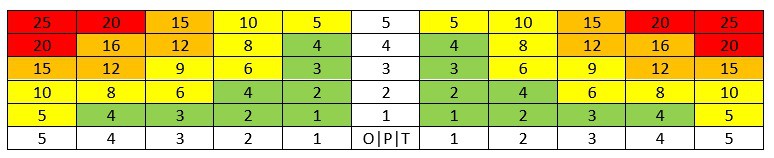
So green means accepting the situation for both opportunities and threats. You leave it at that. Red means that you tackle things: reduce risks or… and strengthen opportunities or… Yellow and orange are in between. This risk matrix is the implementation of the formula
R = P x I
With R = risk, P = total probability and I the impact.
The actual evaluation of the risk is the placement of this risk on this risk matrix.
The prioritization of the risks is done by means of a risk register, in which the situation is summarized and the risks with the highest R-values, i.e., the highest importance, are placed at the top.
Such a simple risk register contains the following fields:
- Process, project or service
- Cause
- Event
- Effect
- Probability
- Impact
- Risk value (in descending value)
- Additions for the following progress are:
- Strategy: accept, share, mitigate, remove the goal
- Measure
- Owner of the measure
- Deadline
- Residual risk fields
Determining, implementing, and following up measures
As indicated, the risk register contains a field for the indication of the measure(s).
In simple terms, there are two types of measures: preventive measures and protective measures.
Preventive measures serve to create a blockage between the cause and the threatening event. It reduces the probability or makes it zero. For the opportunities, it maximizes the probabilities.
Protective measures serve to create a blockage between the threatening event and the maximum possible consequences. It reduces the impact of the consequences or makes them non-existent. For an opportunity, it maximizes the effects.
Usually, the package consists of both preventive and protective measures.
Report
The owner of the process or project reports to the owner of the risks. This is often the CRO who then submits the risk report to and discusses it with the CEO and provides feedback down the hierarchy.
It uses a template that contains at least the following topics:
- Management summary.
- Scope of the risk study.
- Possible total impact if nothing is done.
- Overview of the measures and those responsible for implementation, with estimated budget per person responsible for his measures and a required total budget.
- Proposal of action in a timetable.
- Attachments:
- Risk register.
- Budgets per measure.
What after the basic tasks?
A thorough elaboration of ISO 31000 is one of the possibilities. To do this, you process the above steps in a prescribed PDCA cycle (Plan-Do-Check-Act). It is best to first gain experience with the basic steps before you start working on the policy document. This approach is useful to have the policy directly adapted to the concrete operation in the organization.